As we step into 2024, the digital landscape is evolving at an unprecedented pace. With more devices connected than ever before, the need for robust cybersecurity measures has never been more urgent. I’ve been keeping a close eye on the latest trends, and here are five that I believe will be crucial in protecting your data this year.
The Rise of AI in Cybersecurity
Artificial Intelligence (AI) is no longer just a buzzword; it’s a game-changer in the world of cybersecurity. AI-driven tools can analyze vast amounts of data in real-time, identifying patterns and anomalies that might indicate a security breach. For instance, AI can detect phishing emails with uncanny accuracy, often before they even reach your inbox. This proactive approach is a significant leap from traditional reactive methods, which often leave you vulnerable until it’s too late.
One example of AI in action is the use of machine learning algorithms to predict and prevent cyberattacks. Companies like Microsoft and Google are already leveraging AI to enhance their security systems. Imagine a world where your data is protected 24/7 by a vigilant AI guard, constantly learning and adapting to new threats. It’s not just a possibility; it’s becoming a reality.
The Growing Importance of Zero Trust Architecture
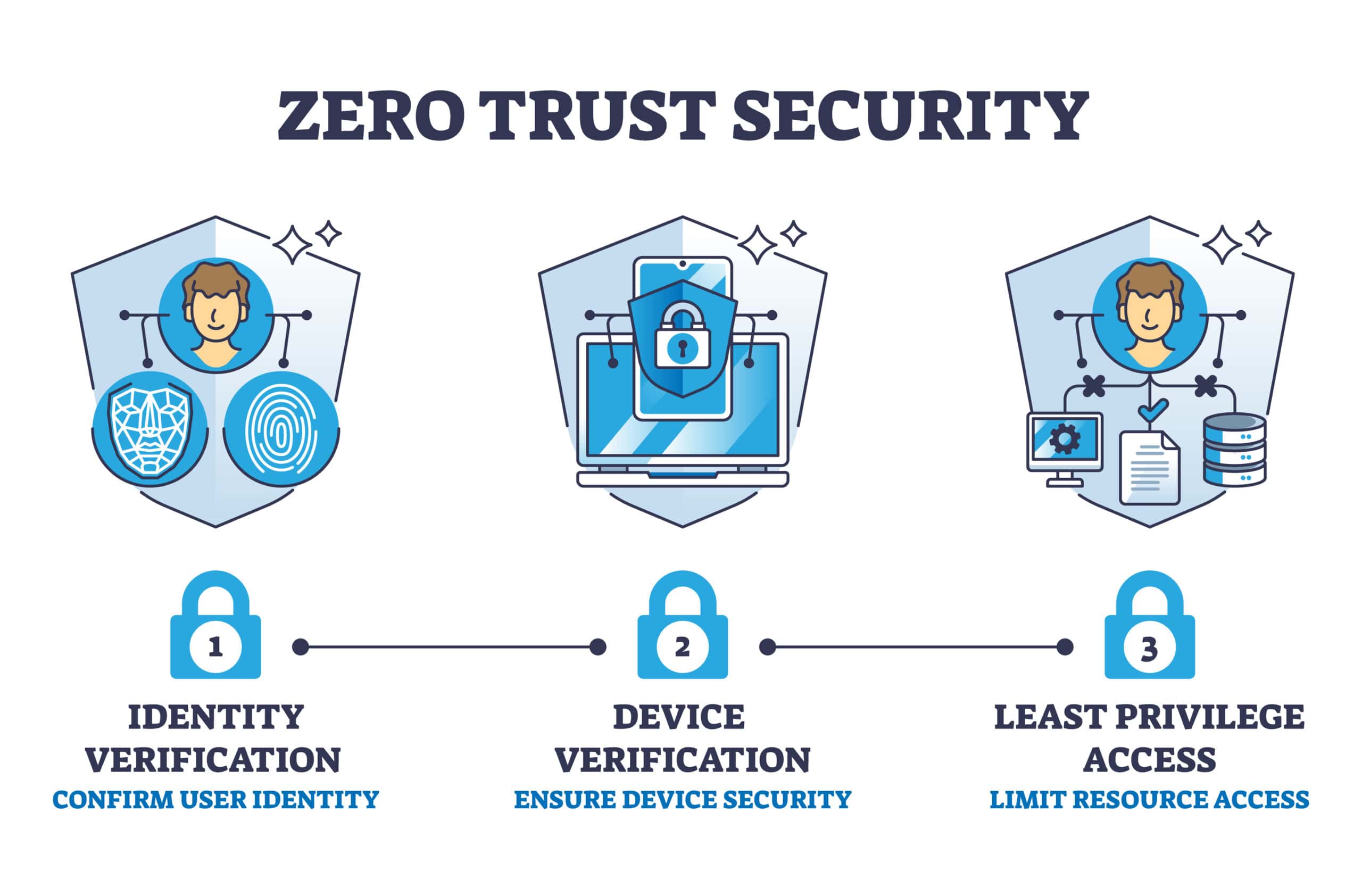
Zero Trust Architecture (ZTA) is gaining traction as a critical component of cybersecurity strategies. The core principle of ZTA is simple: never trust, always verify. This means that every access request, whether from inside or outside your network, is treated as a potential threat until proven otherwise. It’s a shift from the traditional “trust but verify” model, which has proven to be insufficient in today’s complex digital environment.
For example, let’s say you have an employee working remotely. Under a Zero Trust model, that employee’s device would be continuously monitored and verified before being granted access to sensitive data. This approach minimizes the risk of insider threats and external breaches, providing a much-needed layer of security.
The Evolution of Multi-Factor Authentication

Multi-Factor Authentication (MFA) has been around for a while, but its importance is only growing. In 2024, we’re seeing MFA evolve into more sophisticated and user-friendly forms. Gone are the days of cumbersome authentication processes that require you to remember multiple passwords or carry around a physical token. Today, MFA can be as simple as a fingerprint scan or a facial recognition check.
One notable example is the integration of biometric authentication with MFA. Companies like Apple and Samsung are leading the charge, offering seamless and secure access to their devices and services. This not only enhances security but also improves the user experience, making it easier for everyone to protect their data.
The Impact of Quantum Computing on Cybersecurity

Quantum computing is on the horizon, and its potential impact on cybersecurity is both exciting and daunting. While quantum computers have the power to revolutionize various industries, they also pose a significant threat to current encryption methods. Traditional encryption algorithms, which rely on the difficulty of solving complex mathematical problems, could be rendered obsolete by quantum computing.
To prepare for this, researchers are already developing quantum-resistant encryption techniques. These new methods are designed to withstand the computational power of quantum computers, ensuring that your data remains secure even in a post-quantum world. It’s a race against time, but the stakes couldn’t be higher.
The Role of Blockchain in Data Protection
Blockchain technology is best known for its role in cryptocurrencies, but its potential in cybersecurity is equally significant. Blockchain’s decentralized and immutable nature makes it an ideal solution for data protection. By distributing data across a network of nodes, blockchain eliminates the single point of failure that is common in traditional systems.
One practical example is the use of blockchain for securing supply chain data. Companies like IBM are already implementing blockchain solutions to ensure the integrity and authenticity of their products. This not only protects against cyber threats but also builds trust with customers by providing transparency and accountability.
Comparing Traditional vs. Modern Cybersecurity Methods
| Aspect | Traditional Methods | Modern Methods |
|---|---|---|
| Detection | Reactive; relies on signatures and patterns | Proactive; uses AI and machine learning for real-time analysis |
| Access Control | Trust but verify; perimeter-based | Zero Trust; continuous verification of every access request |
| Authentication | Single-factor; password-based | Multi-factor; includes biometrics and other advanced methods |
| Encryption | Traditional algorithms; vulnerable to quantum computing | Quantum-resistant algorithms; designed to withstand quantum threats |
| Data Distribution | Centralized; single point of failure | Decentralized; blockchain technology for distributed and immutable data storage |
In conclusion, the cybersecurity landscape is rapidly evolving, and staying ahead of the curve is essential for protecting your data in 2024. By embracing these emerging trends—AI, Zero Trust Architecture, advanced MFA, quantum-resistant encryption, and blockchain—you can ensure that your digital assets remain secure in an increasingly complex and interconnected world.









